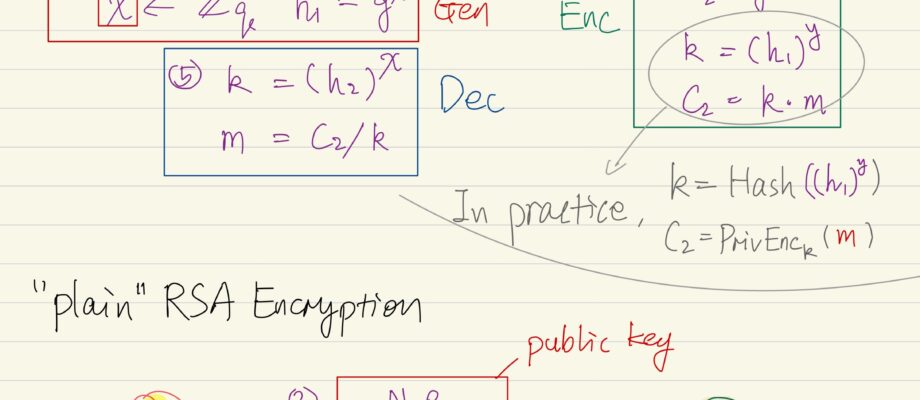
A public-key encryption scheme is composed of three probabilistic polynomial time algorithms: Gen The key-generation algorithm that on input 1n (where n is security parameter), outputs public key pk, and private key sk. Enc Encryption algorithm that on input pk and a message m, outputs a cipher text c. Dec Decryption algorithm that on input … Continue reading Public Key Encryption
0 Comments