Public Key Infrastructures & SSL/TLS
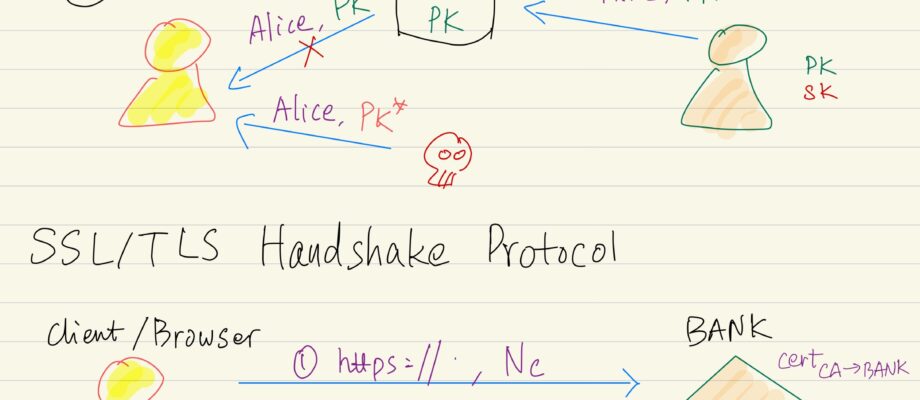
An attacker can try to manipulate the public key distribution process. In particular nothing prevents an attacker from inserting attacker’s public key pk* into the public database but claiming other’s name in order to overwrite the original public key pk. Moreover, the attacker may prevent or block the communication from any party from reaching the … Continue reading Public Key Infrastructures & SSL/TLS
0 Comments