Networking in Google Cloud: Defining and Implementing NetworksGoogle Cloud In the era when everything goes virtual, private networks in public cloud is one of the most essential and attractive part of cloud computing. They usually have a fancy name “Virtual Private Cloud” or VPC, available in the catalog of almost all Cloud service providers. This…
Implementing Networks in Google Cloud
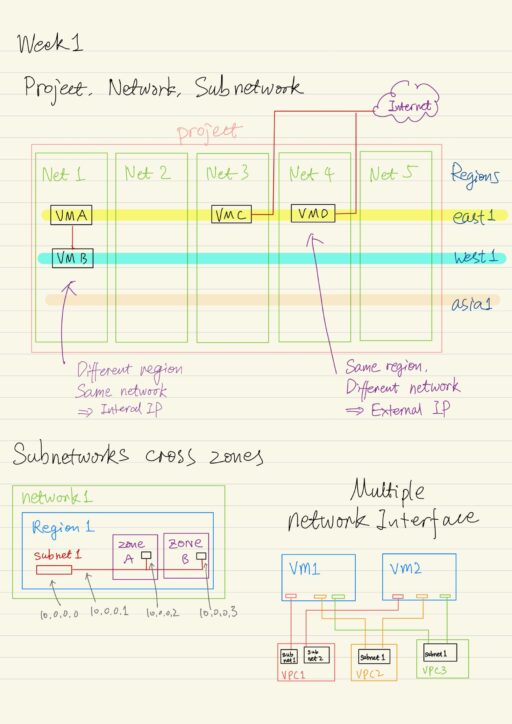
GCP uses a software defined network, that is build on top of a global fiber infrastructure, which makes GCP one of the world’s largest and fastest networks. Thinking about resources as services, rather than as hardware, will help you understand the options that are available and their behavior. Google Cloud is organized into regions and zones, for…
My #92 course certificate from Coursera
Introduction to Virtual RealityGoldsmiths, University of London Recently, Metaverse is a buzz on the Internet. Quite a lot people talk about it. There are interest, concerns, dismissal, criticism, or whatever. It is one’s personal taste. Once my out-of-fashion understanding of Virtual Reality was no more than gaming console. But this course opened my eyes to…
Linear Regression
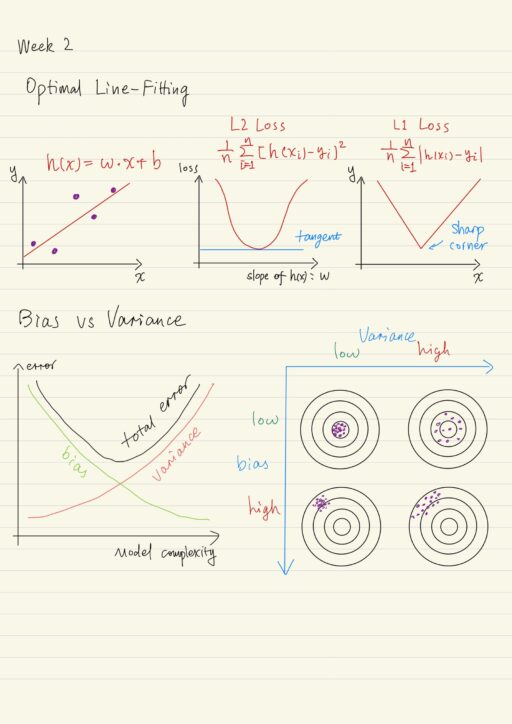
Recall that the concept of hypothesis spaces is a collection of hypotheses that might answer a particular question, and learning algorithms find the best hypothesis in the space of functions which we’ll call the model or QuAM. Previously we learned that classification learning algorithms operate in the space of functions that classify examples. However we can also think…
My #91 course certificate from Coursera
Architecting with Google Kubernetes Engine: FoundationsGoogle Kubernetes and its ecosystem provide all the capabilities needed to address key concerns of any microservice architecture. It is hot ever since its debut in 2014 from Google, and now is widespread and be supported by many big companies. I have been working on Kubernetes and Redhat’s distribution Openshift Container…
Virtual Reality and Psychology
How to define virtual reality? Different people has different experiences. In order to describe these experiences, we often use terms such as immersive, engaging, and interactive. The user is effectively immersed in a responsive virtual world. Fred Brooks VR Hardware This implies the user has dynamic control of their viewpoint, which is something at the…
My #90 course certificate from Coursera
CryptographyUniversity of Maryland College Park This course is definitely one of the best that you shouldn’t miss out on. It is a wide-ranging course covering tons of topics, meanwhile many of them are taught in depth. I love the syllabus, the pace, and the internal logic among different modules. Learning this course is an amazing…
Public Key Infrastructures & SSL/TLS
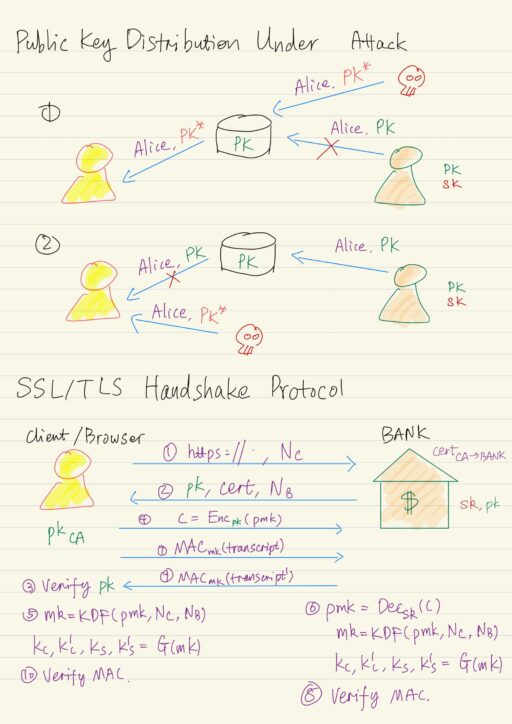
An attacker can try to manipulate the public key distribution process. In particular nothing prevents an attacker from inserting attacker’s public key pk* into the public database but claiming other’s name in order to overwrite the original public key pk. Moreover, the attacker may prevent or block the communication from any party from reaching the…
Discrete Logarithm Based Digital Signature
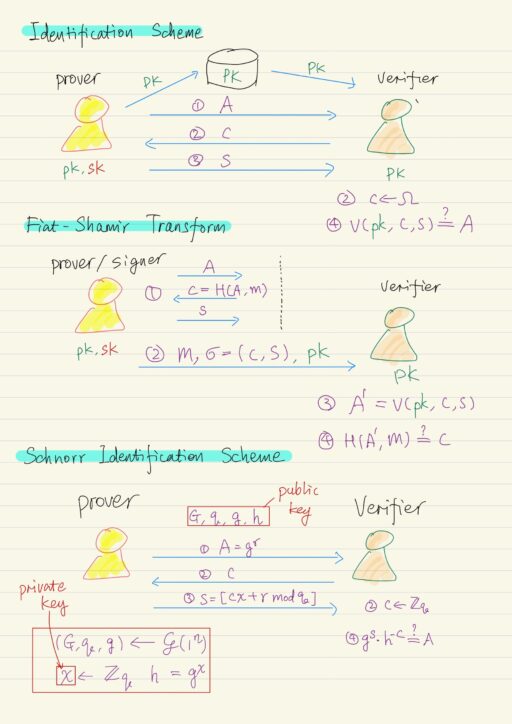
Identification Schemes Identification schemes are extremely important as building block for digital signature scheme. An identification scheme is a protocol that is running in the public key setting. There are two parties: prover and verifier. Prover Generates a pair of public and private keys.Publicize their public keys. Verifier Obtain authentic copy of the prover’s public…
Digital Signature
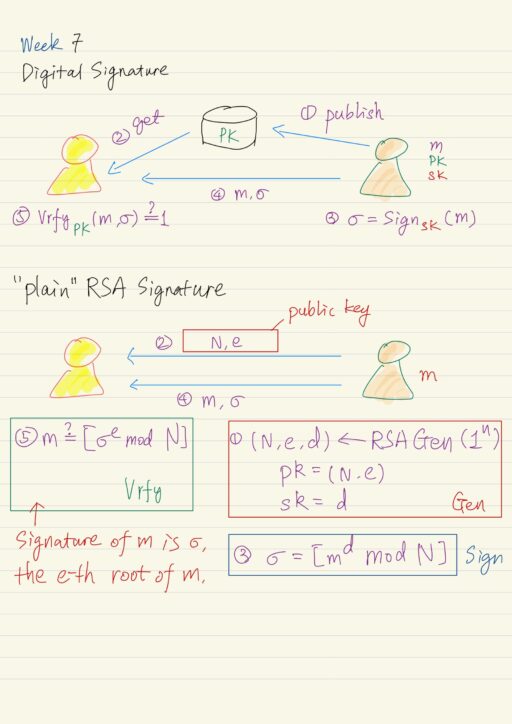
Digital signature is a mechanism that can be used to provide integrity in the public key setting, analogous to message authentication codes in the private key setting. However there is some key differences between the both. How does digital signature work? Digital signature Public key encryption Sender Party has the private key Party has the…
Public Key Encryption
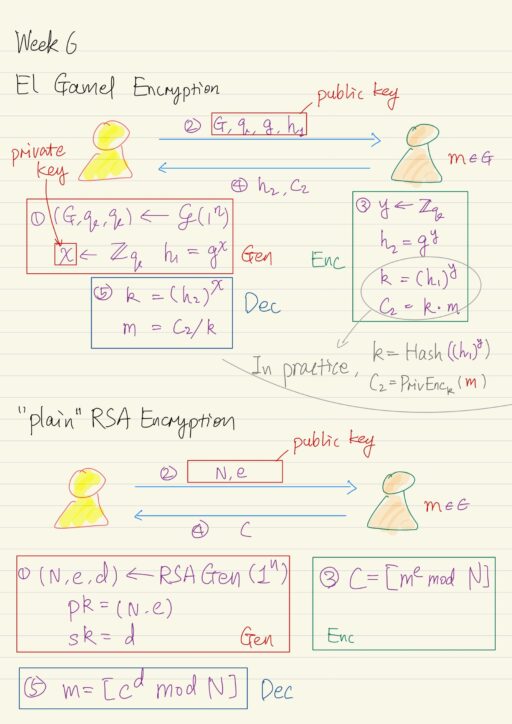
A public-key encryption scheme is composed of three probabilistic polynomial time algorithms: Gen The key-generation algorithm that on input 1n (where n is security parameter), outputs public key pk, and private key sk. Enc Encryption algorithm that on input pk and a message m, outputs a cipher text c. Dec Decryption algorithm that on input…
My #89 course certificate from Coursera
Federal Taxation I: Individuals, Employees, and Sole ProprietorsUniversity of Illinois at Urbana-Champaign I believe taxation is the negotiation between the governors and the governed. Yep, most of people don’t like taxes, however it is really rewarding if you know how the intricacies work. This is an “WOW” course that deserves your attention. Lots of stuff…
Itemized Deductions and Retirement Plans
Recall that the itemized deductions are also called “from AGI” deductions or below the line deductions. They are usually more personal in nature, including medical, taxes, interest and charitable, and not related to running a trade or business. It only provide a tax benefit to the extent, in total, they exceed the standard deduction amount….
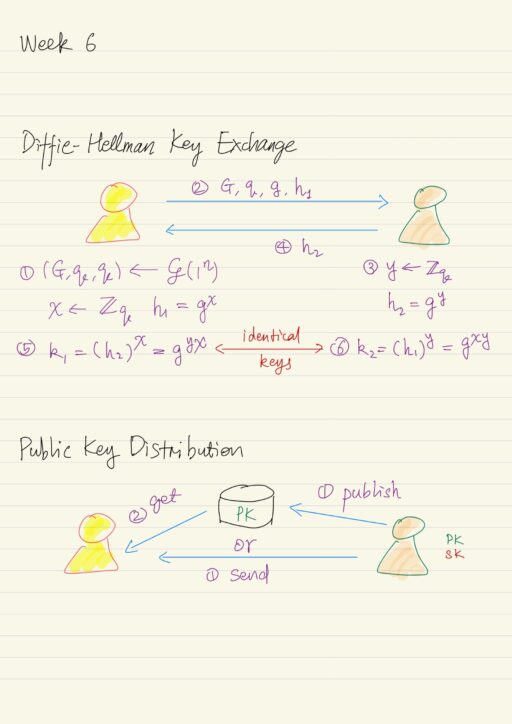
Public Key Revolution
A New Direction in Cryptography Recall that the private-key cryptography allows two users who share a secret to establish a “secure channel” which is a way to communicate with both secrecy and integrity. But the problem is that the need to share this secret key incurs several drawbacks. “Classical” private key cryptography offers no solution…
Business Deductions
Employees vs Self-Employed What differentiates an employee from a self-employed individual (also known as independent contractor)? Employee If a person is subject to the will and control of another with respect to what job shall be done and how it shall be done. Then that person is more likely to be considered an employee rather than a self-employed…