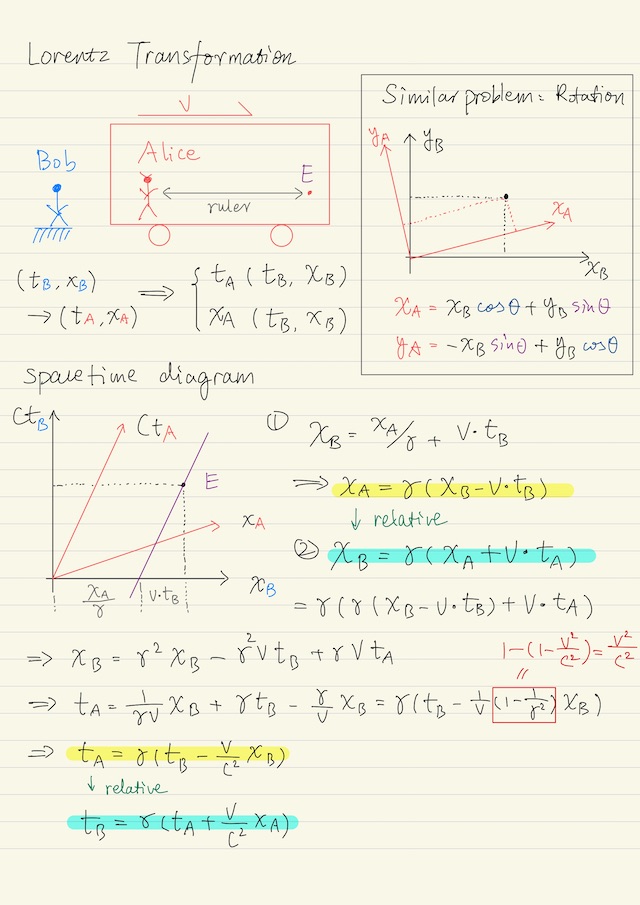
Lorentz transformation is the central question in the mathematical structure of special relativity. Simply put, given the coordinate of the event in one frame, say Bob’s frame, (tB,xB), calculate the coordinate in another frame, say Alice’s frame (tA,xA). Let us first examine a similar problem, which is the rotation of the space directions. In the…
Category: Quick Recap
Fashion & Luxury: Products Development, Communication, Retail
Products Development There is a major difference between luxury and fashion companies in dealing with the product development process. Luxury 1. Most of the products are not seasonal and therefore at the end of the season are not discounted.2. Some products (say, leather goods) have a longer product life cycle. They are iconic, timeless, and…
The Keras Functional API
The reason you might want to use the Functional API (instead of the Sequential API) is if you need more flexibility. For example, you are using: multiple inputs and outputs in a multitask learning model, or conditioning variables. complicated non-linear topology with layers feeding to multiple other layers. With the Sequential API, we didn’t have…
Special Relativity: Length and Simultaneity
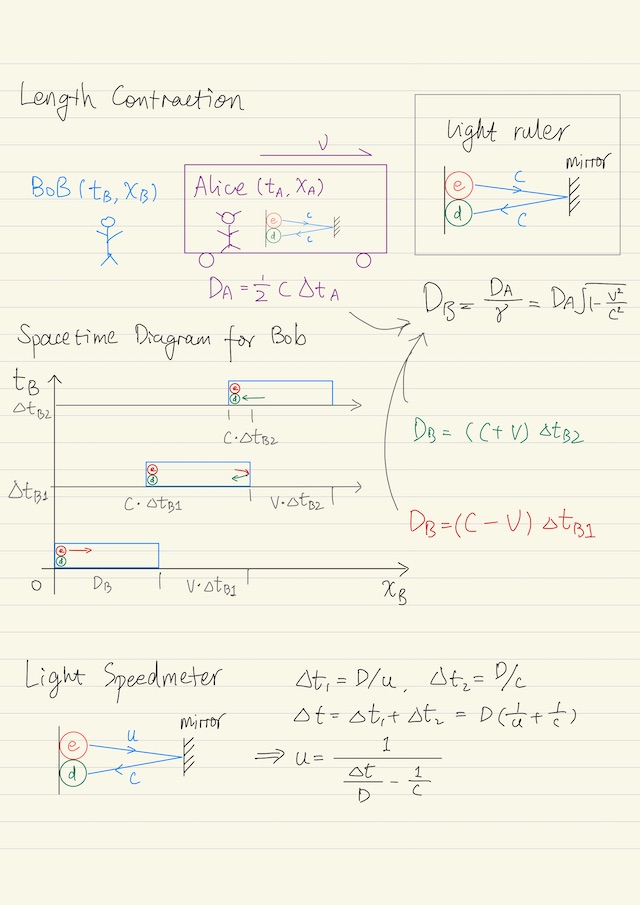
The concept of “length” and “the same time” have to be reconsidered in special relativity. Light Ruler and Length Contraction In the example of the explosion of a grenade, it takes time ∆t from triggering to exploding. If it is triggered and immediately thrown with speed v, how long the grenade travels depends on your…
Fundamentals of Network Communication
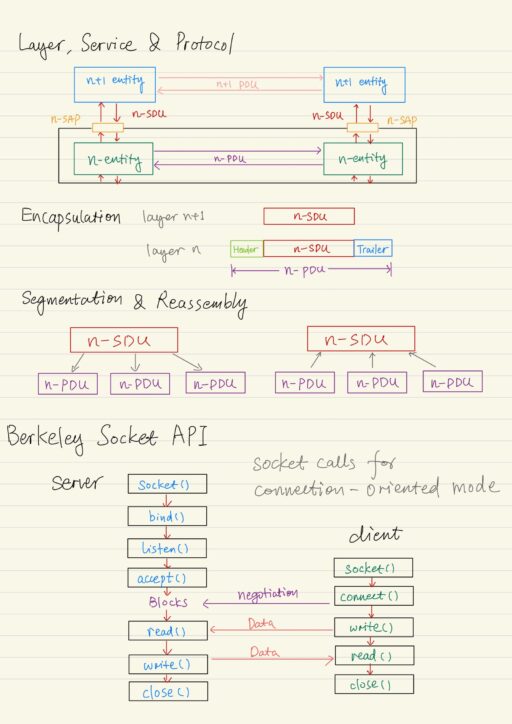
Simply put, a communication network is a set of equipment (routers, servers, switches, etc) and facilities (copper wires, optical fiber) that provide communication services, to transfer information between locations. Evolution of Communication Networks In the history, the evolution of services influence the design of network architecture: Telegraph networks A message is transmitted using signals (drums,…
Regression and Classification Model Assessment
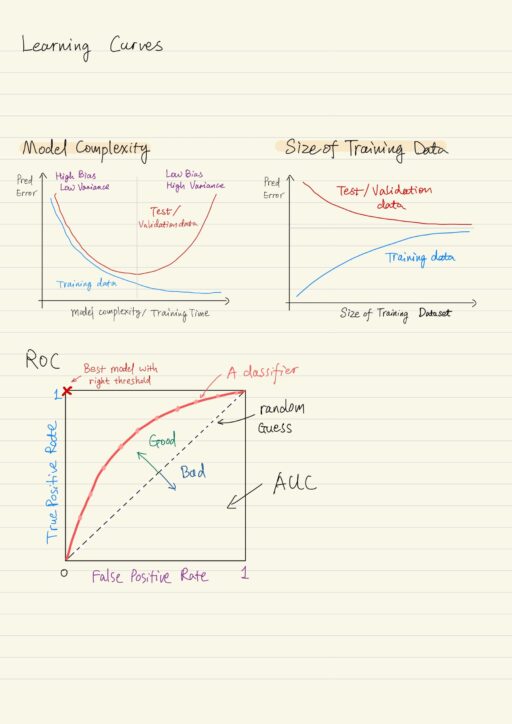
Let’s take a look at how the performance of regression and classification models can be quantified so that we can identify the best learning algorithm to build the model. Most importantly, the learning data should be split into training data and test dtaa. Failing to hold out test data will lead to dire consequences. Regression…
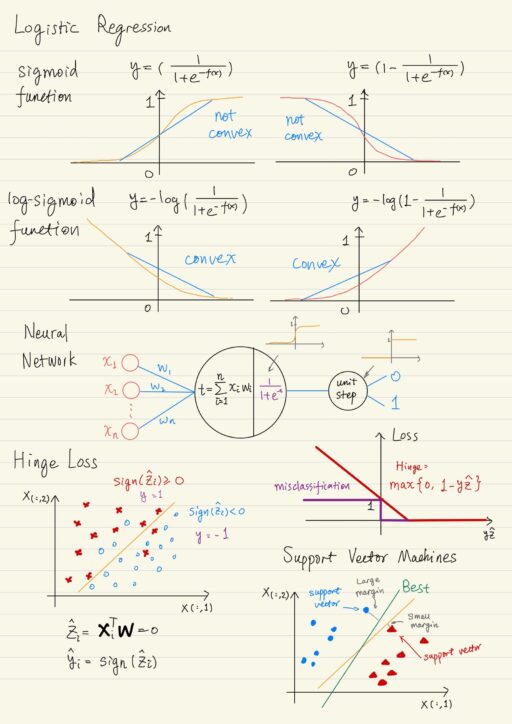
Logistic Regression & Support Vector Machines
Often, some of the “shifts” we need to make when we’re using regression based approaches for classification. There is a major family of classification algorithms called Logistic Regression. Logistic Regression Logistic regression is actually a classification, it does not answer questions with a real number, it answers with a binary category 0 or 1. It…
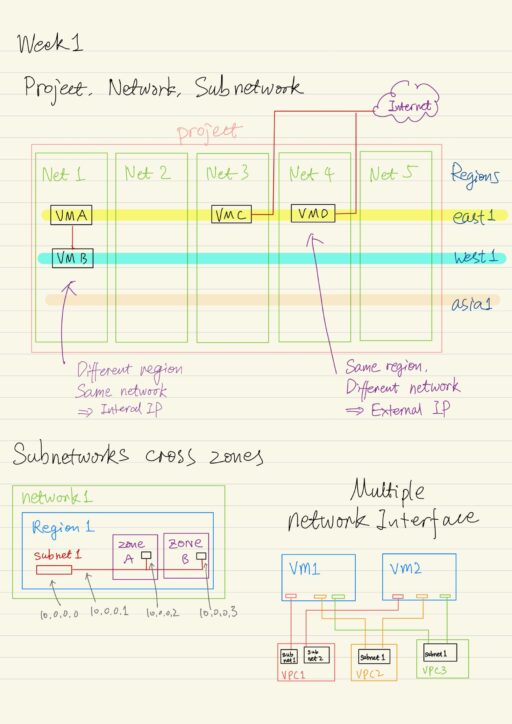
Implementing Networks in Google Cloud
GCP uses a software defined network, that is build on top of a global fiber infrastructure, which makes GCP one of the world’s largest and fastest networks. Thinking about resources as services, rather than as hardware, will help you understand the options that are available and their behavior. Google Cloud is organized into regions and zones, for…
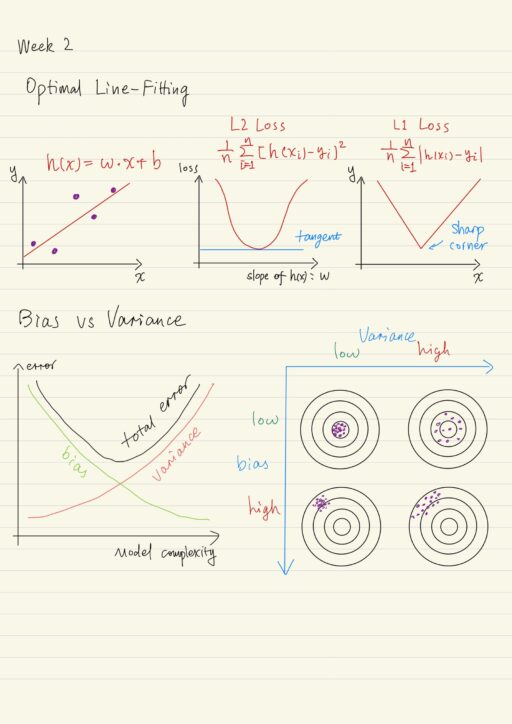
Linear Regression
Recall that the concept of hypothesis spaces is a collection of hypotheses that might answer a particular question, and learning algorithms find the best hypothesis in the space of functions which we’ll call the model or QuAM. Previously we learned that classification learning algorithms operate in the space of functions that classify examples. However we can also think…
Virtual Reality and Psychology
How to define virtual reality? Different people has different experiences. In order to describe these experiences, we often use terms such as immersive, engaging, and interactive. The user is effectively immersed in a responsive virtual world. Fred Brooks VR Hardware This implies the user has dynamic control of their viewpoint, which is something at the…
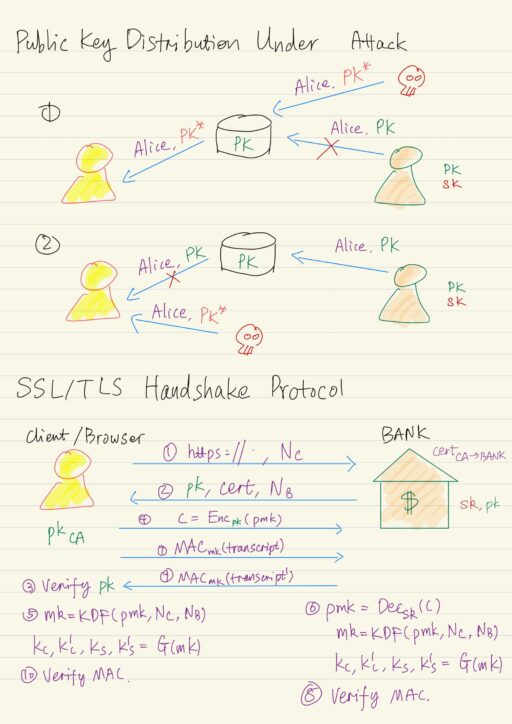
Public Key Infrastructures & SSL/TLS
An attacker can try to manipulate the public key distribution process. In particular nothing prevents an attacker from inserting attacker’s public key pk* into the public database but claiming other’s name in order to overwrite the original public key pk. Moreover, the attacker may prevent or block the communication from any party from reaching the…
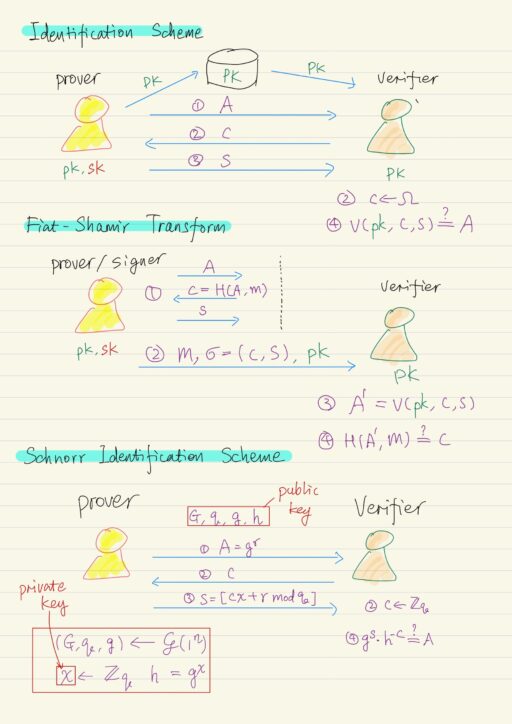
Discrete Logarithm Based Digital Signature
Identification Schemes Identification schemes are extremely important as building block for digital signature scheme. An identification scheme is a protocol that is running in the public key setting. There are two parties: prover and verifier. Prover Generates a pair of public and private keys.Publicize their public keys. Verifier Obtain authentic copy of the prover’s public…
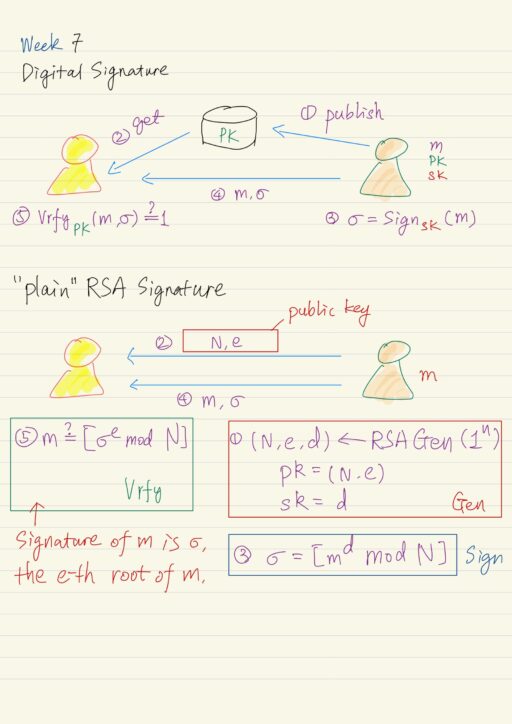
Digital Signature
Digital signature is a mechanism that can be used to provide integrity in the public key setting, analogous to message authentication codes in the private key setting. However there is some key differences between the both. How does digital signature work? Digital signature Public key encryption Sender Party has the private key Party has the…
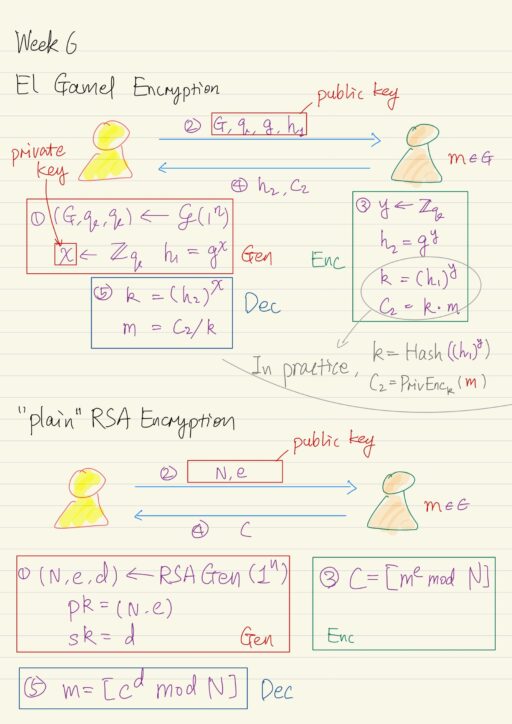
Public Key Encryption
A public-key encryption scheme is composed of three probabilistic polynomial time algorithms: Gen The key-generation algorithm that on input 1n (where n is security parameter), outputs public key pk, and private key sk. Enc Encryption algorithm that on input pk and a message m, outputs a cipher text c. Dec Decryption algorithm that on input…
Itemized Deductions and Retirement Plans
Recall that the itemized deductions are also called “from AGI” deductions or below the line deductions. They are usually more personal in nature, including medical, taxes, interest and charitable, and not related to running a trade or business. It only provide a tax benefit to the extent, in total, they exceed the standard deduction amount….