A New Direction in Cryptography Recall that the private-key cryptography allows two users who share a secret to establish a “secure channel” which is a way to communicate with both secrecy and integrity. But the problem is that the need to share this secret key incurs several drawbacks. “Classical” private key cryptography offers no solution…
Category: Quick Recap
Business Deductions
Employees vs Self-Employed What differentiates an employee from a self-employed individual (also known as independent contractor)? Employee If a person is subject to the will and control of another with respect to what job shall be done and how it shall be done. Then that person is more likely to be considered an employee rather than a self-employed…
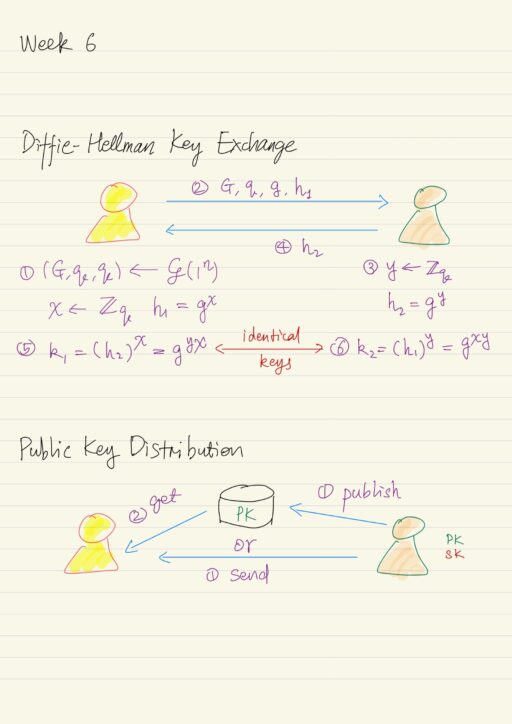
Factoring, RSA, Discrete-Logarithm and Diffie-Hellman
Problems like addition, multiplication, modular arithmetic, exponentiation can be solved in polynomial time, so they are seen as easy problem. Factoring a random number seems not hard, because 50% of the time, random number is even; 1/3 of the time, random number is divisible by 3. But the problem of factoring some special numbers can…
Number Theory and Group Theory
Number theory studies integers and operation on them. Basics of number theory have natural application, like addition, subtraction, etc. However advanced number theory topic has been praised as a branch of pure mathematics, mathematics for itself. This does not mean the number theory is useless. Things changed dramatically in computer era. … virtually every theorem…
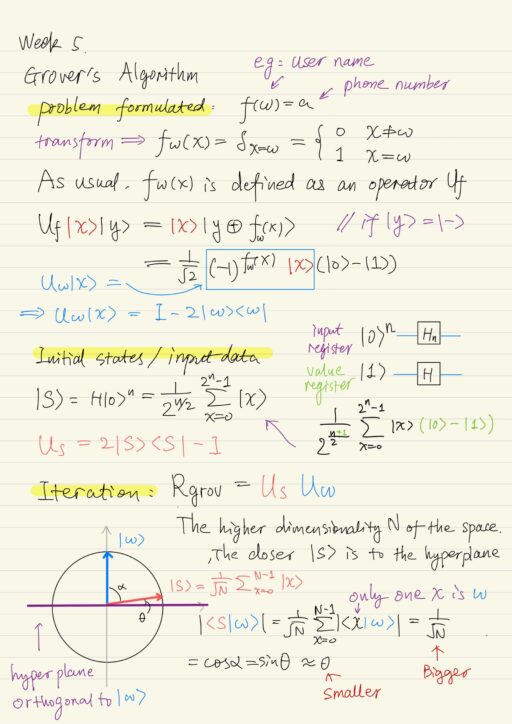
Grover’s Algorithm
Brute-force is apparently applicable to any problem of NP, since if you have some candidate for an answer, you can easily check / verify this candidate (but finding a candidate is still hard). For example: given a phone number to find its owner in the phone book, you can easily check it, but you need…
Shor’s Algorithm
Nowadays, probably Peter Shor’s algorithm for function period finding is the most significant achievement in the field of quantum computing. It allows us to factor big composite numbers in polynomial time. However for the classical computations, this problem is believed to be hard. For a big number N = p × q, where p and…
Tax Deductions for Business, Hobby & Rental
Deductions are essentially the tax word for expense that can reduce the tax base. Deductions are disallowed unless a specific provision permits them. Deductibility depends on “legislative grace”. That is what Congress has decided to legislatively decree what is an allowable expense that can reduce the tax base. As a result, deductions are defined quite narrowly….
Deutsch’s Problem and DIY a Quantum Computer
The first algorithm ever designed for a quantum computer, is the algorithm for solving Deutsch’s problem. The algorithm is an illustration for the mathematical model of quantum computing. Deutsch’s Problem Deutsch’s problem is about the function which maps one bit to another bit, i.e. f:{0,1} → {0,1}. There are only 4 types such functions: f(x)…
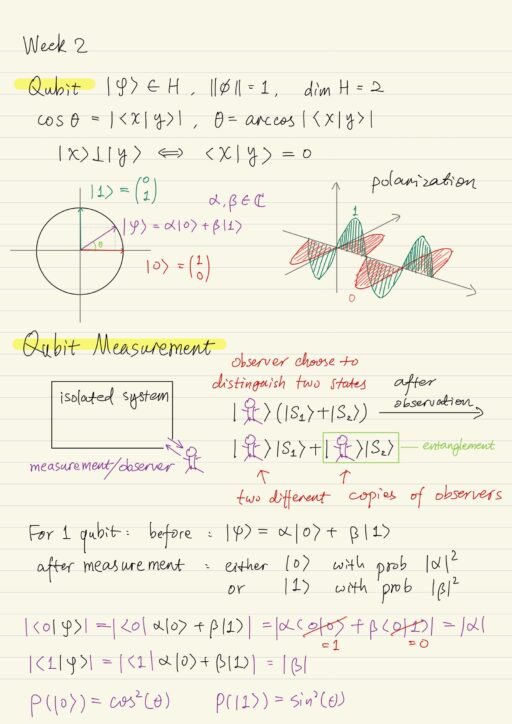
Mathematical Model of Quantum Computing
The mathematical model of quantum computing allows us to understand and design quantum algorithms without any background in quantum mechanics or physical implementation of quantum hardware. The most significant part of the whole theory of quantum computing is qubit, i.e. quantum bit, which is the minimum unit of quantum information. One qubit information can be…
Google SEO Fundamentals
The search engine optimization of a website is divided into three key areas: On-page SEO The term meta data basically means data that describes other data. Each page contains an area of meta data, the area is made up of individual meta tags. These individual meta tags are small snippet of text that helps search…
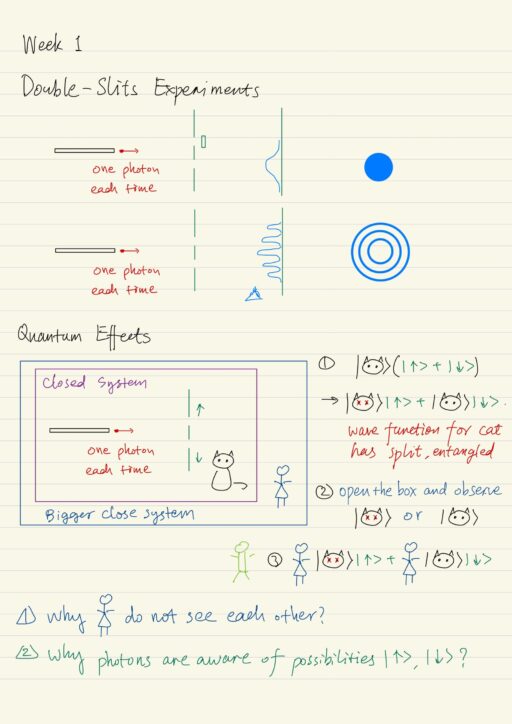
Computation: from Classical to Quantum
The computation is a physical process, which is finite in time with fixed and distinguished set of states. It always consumes or transforms energy meanwhile keeps distinguishable states. Computations transform or process information. Information is actually an interpretation of the particular system states. Two different systems with different states can actually present the same information….
Statistical Thermodynamics
Role of Statistics Statistics is the study of systems that exhibit variability. Because macroscopic systems are composed of atoms and molecules that are in constant motion, what we see at the macroscopic level are averages of that variability. Suppose we knew the kinetic energy of every molecule in a volume, then the average kinetic energy…
Macroscopic Thermodynamics
First of all, a quick introduction to 4 the most important figures in thermodynamics: Sadi Carnot (1796-1832) who discovered the second law of thermodynamics. Rudolf Clausius (1822-1888) who restated the Sadi Carnot’s principle into the form we use today. William Thomson (Lord Kelvin, 1824-1907) who brought thermodynamics into its modern form. Max Planck (1858-1947) who…
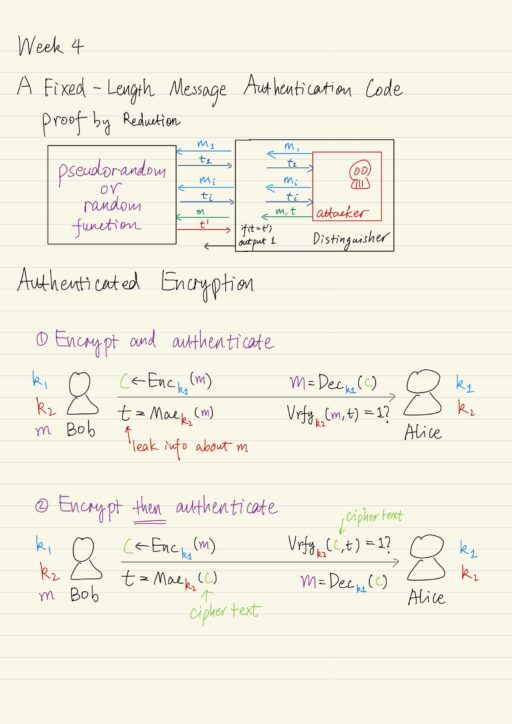
Message Authentication Codes & Authenticated Encryption
Besides the secrecy of communication, we also need to be concerned with integrity, which ensures that a message received by the receiver, originated from the intended sender, and was not modified, even if an attacker controls the channel. The standard error-correction techniques are not enough, because here we are not concerned with random errors, instead…
Google Docs at a Glance
Google Docs is Google’s online processor that is part of Google Workplace. You can create, view, and edit your Google Docs documents all with just a web browser. It’s also easy to share with anyone. It also works well with Microsoft Word files and many other formats. Go to https://docs.google.com to launch Google Docs and…