My #90 course certificate from Coursera
CryptographyUniversity of Maryland College Park This course is definitely one of the best that you shouldn’t miss out...
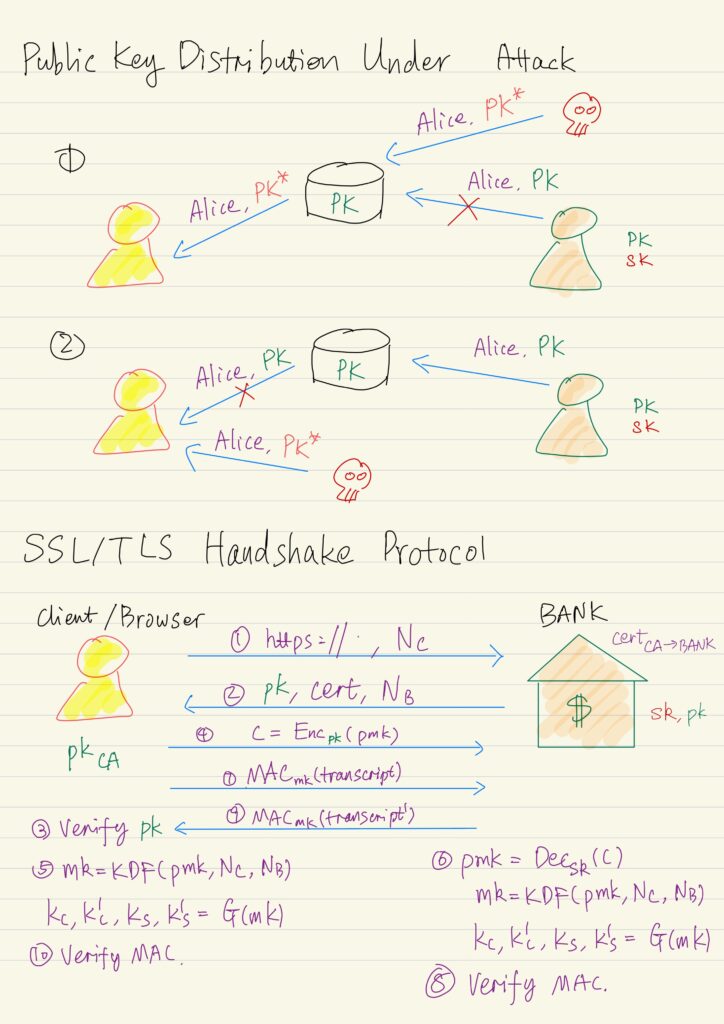
Public Key Infrastructures & SSL/TLS
An attacker can try to manipulate the public key distribution process. In particular nothing prevents an attacker from...
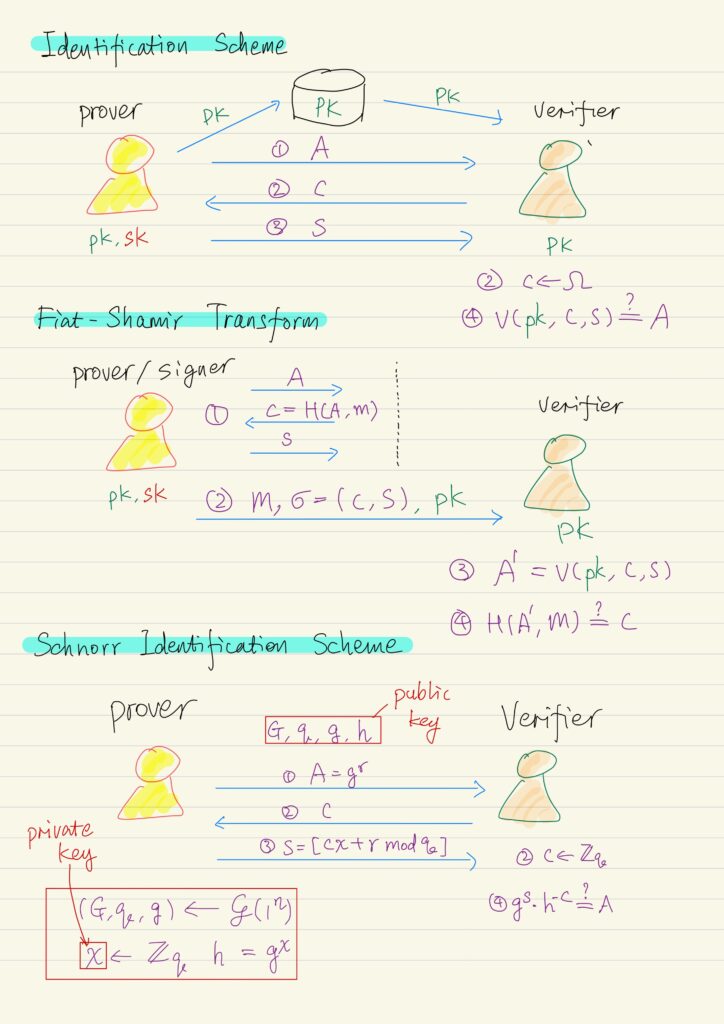
Discrete Logarithm Based Digital Signature
Identification Schemes Identification schemes are extremely important as building block for digital signature scheme. An identification scheme is...
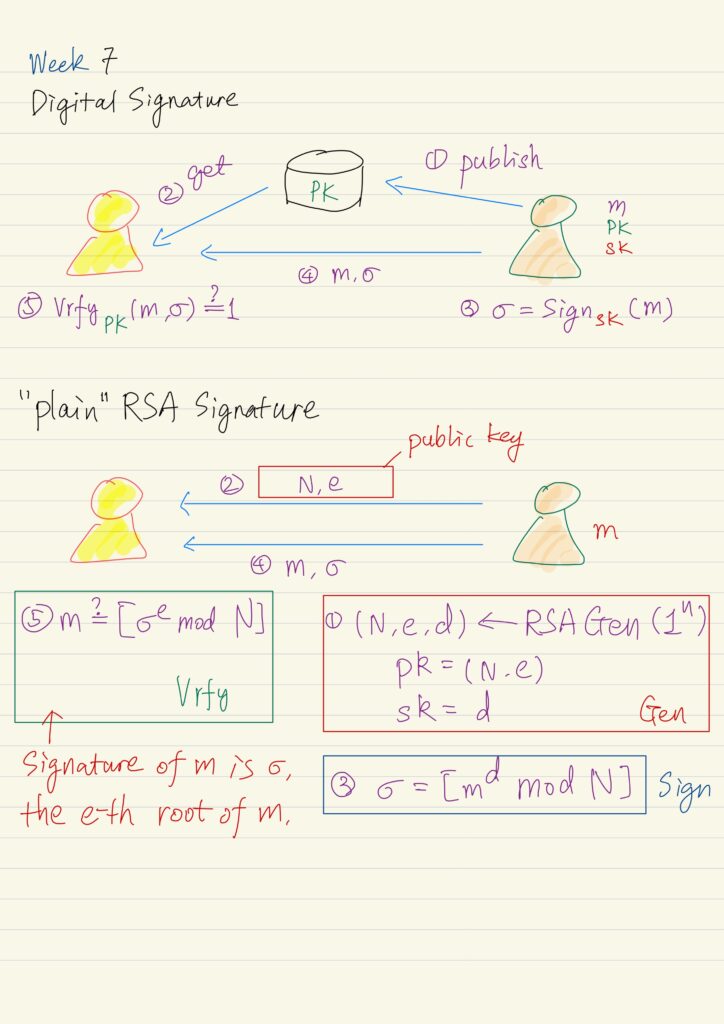
Digital Signature
Digital signature is a mechanism that can be used to provide integrity in the public key setting, analogous...
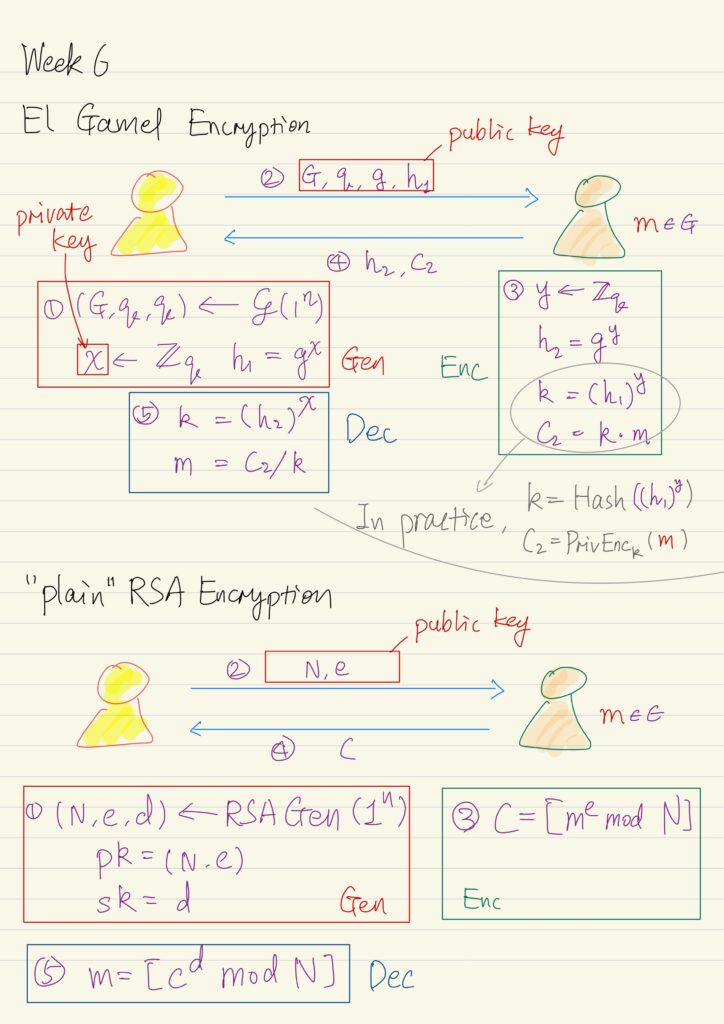
Public Key Encryption
A public-key encryption scheme is composed of three probabilistic polynomial time algorithms: Gen The key-generation algorithm that on...
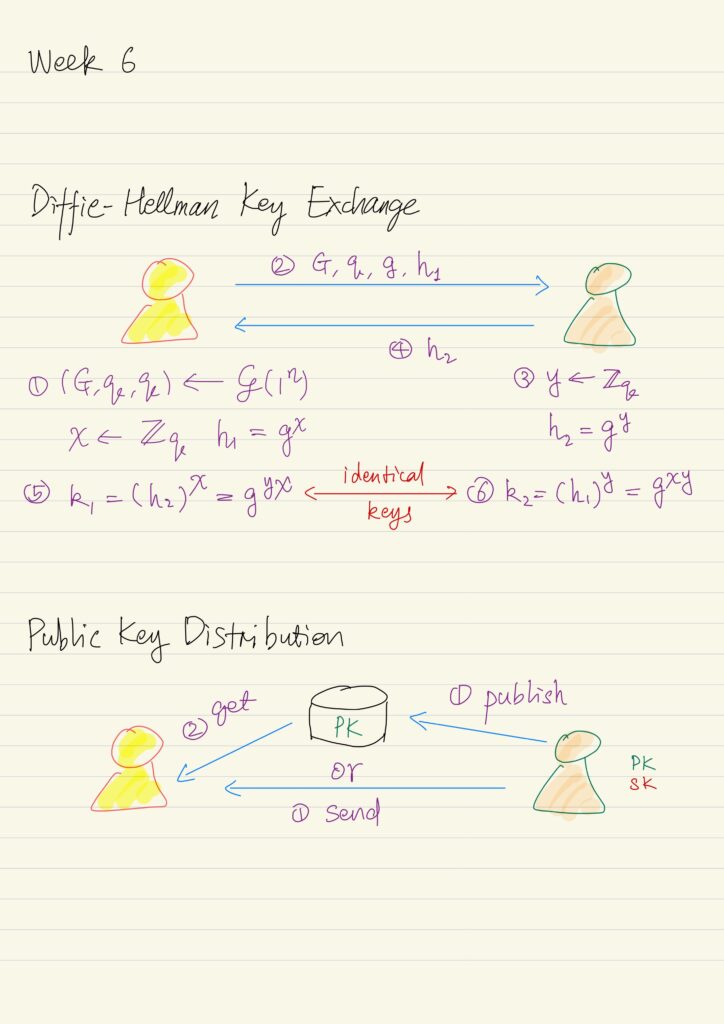
Public Key Revolution
A New Direction in Cryptography Recall that the private-key cryptography allows two users who share a secret to...

Factoring, RSA, Discrete-Logarithm and Diffie-Hellman
Problems like addition, multiplication, modular arithmetic, exponentiation can be solved in polynomial time, so they are seen as...

Number Theory and Group Theory
Number theory studies integers and operation on them. Basics of number theory have natural application, like addition, subtraction,...
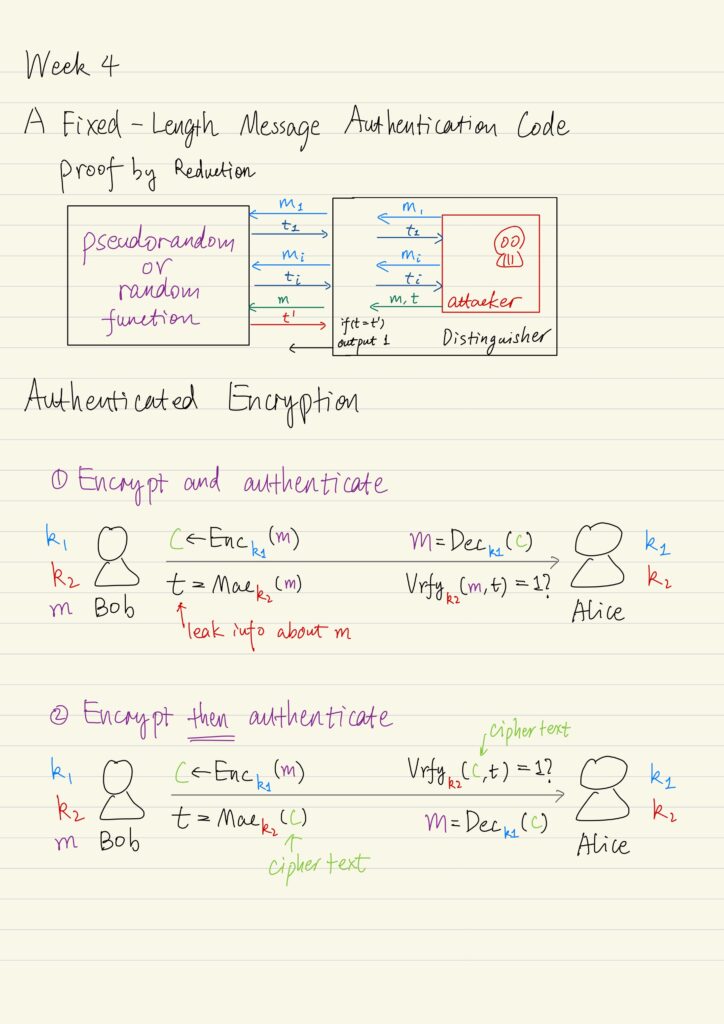
Message Authentication Codes & Authenticated Encryption
Besides the secrecy of communication, we also need to be concerned with integrity, which ensures that a message...
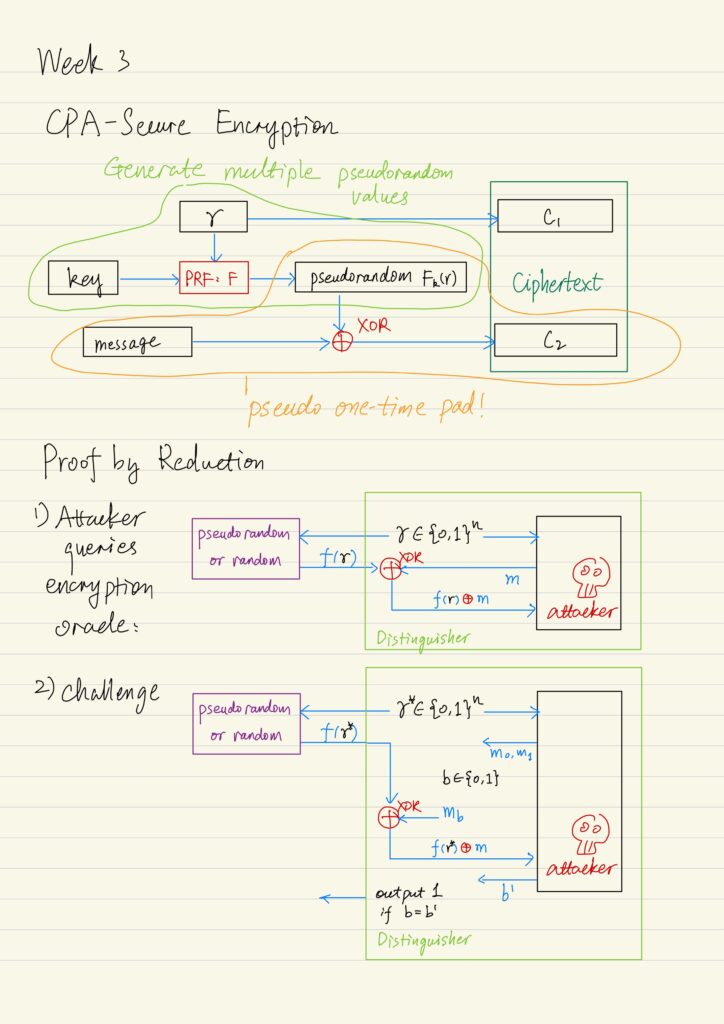
Private Key Encryption
Limitations of Perfect Secrecy Recall that the perfect secrecy has two limitations: The first limitation can be circumvented...
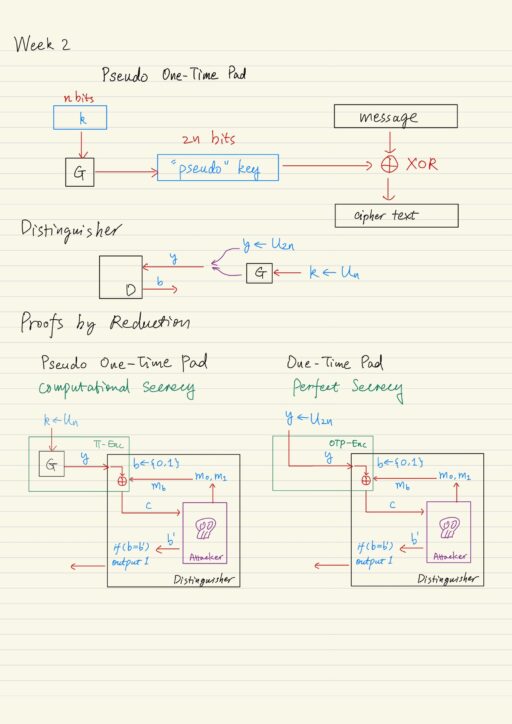
Computational Secrecy, Pseudo-randomness, and Proof of Security
Limitations of the One-Time Pad The one-time pad encryption scheme achieves perfect secrecy, but nowadays it is not...

Introduction to Classical Cryptography
In dictionary, cryptography is defined as the art of writing or solving codes. Historically, cryptography focused exclusively on...